shivajikobardan
- 637
- 54
- Homework Statement
- Confusions on what is actual DES
- Relevant Equations
- None
First I'll give some context about how the book's written as many books are presenting it in different ways.
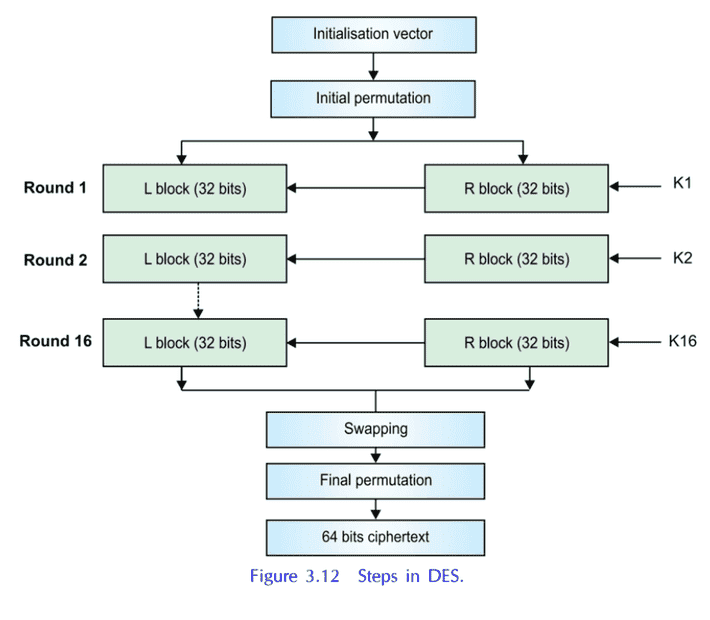

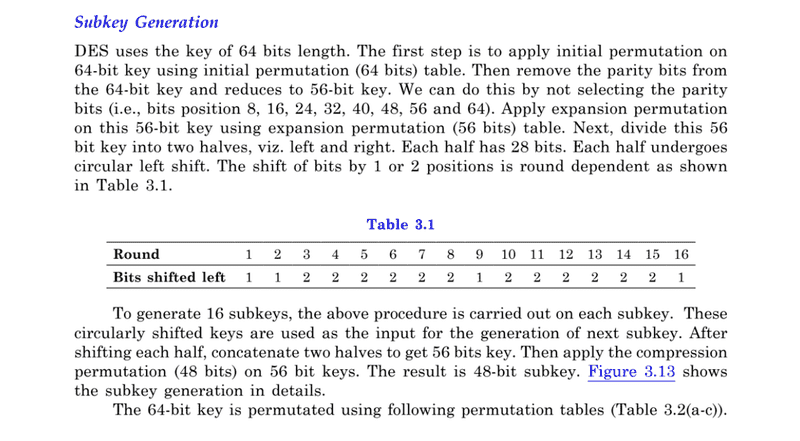
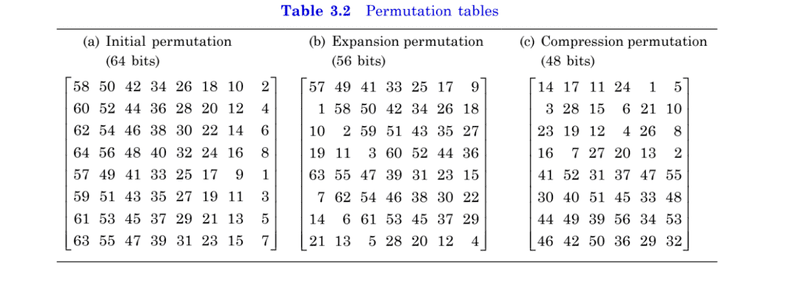
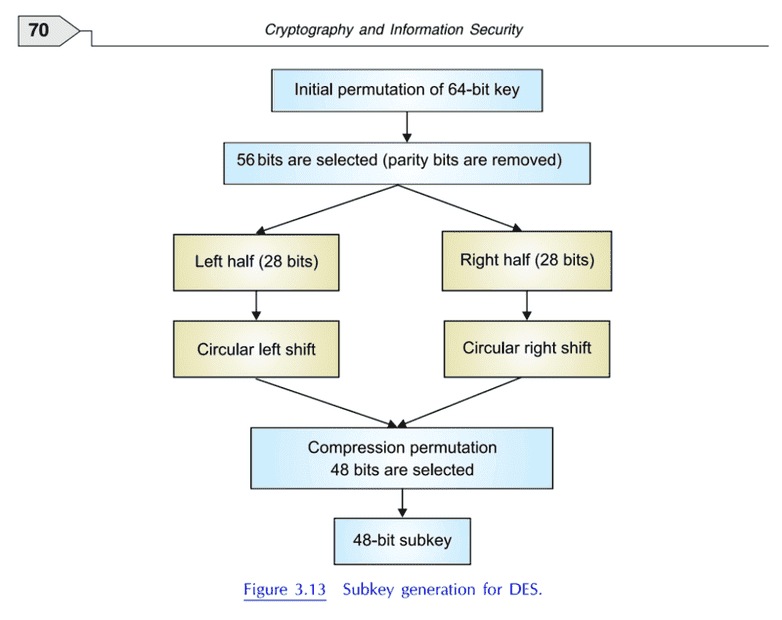

Reference: CRYPTOGRAPHY AND INFORMATION SECURITY, THIRD EDITION
By PACHGHARE, V. K.
Confusions:
1) Why is Expansion Permutation called so? The name sounds very contrary to what what you'd expect a Expansion Permutation to do. You'd expect it to work like say 4:16 decoder.2) Why is Expansion Permutation done here? The number of bits remained the same. What's the difference? Or are we calling after discarding parity bits as "Expansion Permutation"?
3) Plus I'm reading some answers here and there. And I'm hearing that the information that I presented here is wrong.
4) One comment I saw in some other post is that, "(IP) and and (EP) are applied to the plaintext, not the key"
https://en.wikipedia.org/wiki/Data_Encryption_Standard
According to it,
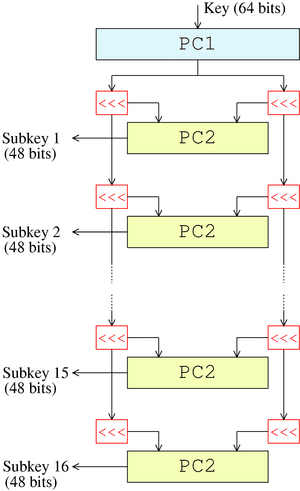
(this figure doesn't really illustrates anything that it claims below) Figure illustrates the key schedule for encryption—the algorithm which generates the subkeys. Initially, 56 bits of the key are selected from the initial 64 by Permuted Choice 1 (PC-1)—the remaining eight bits are either discarded or used as parity check bits. The 56 bits are then divided into two 28-bit halves; each half is thereafter treated separately. In successive rounds, both halves are rotated left by one or two bits (specified for each round), and then 48 subkey bits are selected by Permuted Choice 2 (PC-2)—24 bits from the left half, and 24 from the right. The rotations (denoted by "<<<" in the diagram) mean that a different set of bits is used in each subkey; each bit is used in approximately 14 out of the 16 subkeys.
Wikipedia vs my first source:
a) No initial permutation is done on key.
b) No expansion permutation is done
c) Only left shift happens, no right shift as shown in my first figure.There're some other sources which seem to be taken from wikipedia and sound similar to it. They're given follows.
Others:
1) https://www.lri.fr/~fmartignon/documenti/systemesecurite/4-DES.pdf
Go to page 19.
So, which one should I believe? I think WikiPedia should be believed as many are copying from it, but I'm not sure. Which version is correct according to the actual DES?
2)
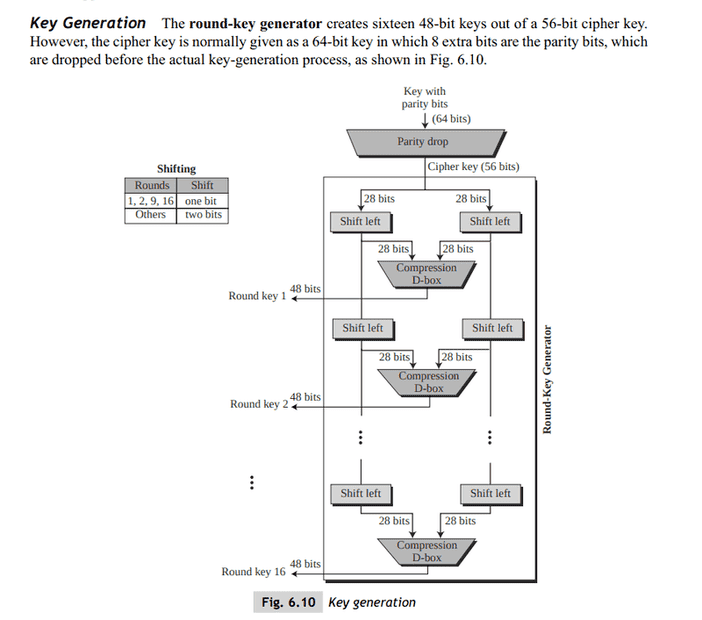
Source: https://academic.csuohio.edu/yuc/security/Chapter_06_Data_Encription_Standard.pdf
Reference: CRYPTOGRAPHY AND INFORMATION SECURITY, THIRD EDITION
By PACHGHARE, V. K.
Confusions:
1) Why is Expansion Permutation called so? The name sounds very contrary to what what you'd expect a Expansion Permutation to do. You'd expect it to work like say 4:16 decoder.2) Why is Expansion Permutation done here? The number of bits remained the same. What's the difference? Or are we calling after discarding parity bits as "Expansion Permutation"?
3) Plus I'm reading some answers here and there. And I'm hearing that the information that I presented here is wrong.
4) One comment I saw in some other post is that, "(IP) and and (EP) are applied to the plaintext, not the key"
https://en.wikipedia.org/wiki/Data_Encryption_Standard
According to it,
(this figure doesn't really illustrates anything that it claims below) Figure illustrates the key schedule for encryption—the algorithm which generates the subkeys. Initially, 56 bits of the key are selected from the initial 64 by Permuted Choice 1 (PC-1)—the remaining eight bits are either discarded or used as parity check bits. The 56 bits are then divided into two 28-bit halves; each half is thereafter treated separately. In successive rounds, both halves are rotated left by one or two bits (specified for each round), and then 48 subkey bits are selected by Permuted Choice 2 (PC-2)—24 bits from the left half, and 24 from the right. The rotations (denoted by "<<<" in the diagram) mean that a different set of bits is used in each subkey; each bit is used in approximately 14 out of the 16 subkeys.
Wikipedia vs my first source:
a) No initial permutation is done on key.
b) No expansion permutation is done
c) Only left shift happens, no right shift as shown in my first figure.There're some other sources which seem to be taken from wikipedia and sound similar to it. They're given follows.
Others:
1) https://www.lri.fr/~fmartignon/documenti/systemesecurite/4-DES.pdf
Go to page 19.
So, which one should I believe? I think WikiPedia should be believed as many are copying from it, but I'm not sure. Which version is correct according to the actual DES?
2)
Source: https://academic.csuohio.edu/yuc/security/Chapter_06_Data_Encription_Standard.pdf