- #1
Frodo
Gold Member
- 201
- 91
- TL;DR Summary
- How do spammers get our names and our email IDs of "me and my friend" so they can send an email to me purporting to be from my friend?
I often receive a spam email sent to me, Frodo <me@example.com>, and purporting to come from a friend of mine, Tom Thumb, whose ID is Tom <my_friend@anymail.com>.
I am sure it isn't random chance as I don't get similar emails from people I don't know.
How does the spammer work out that
Is this possible? Probable? Or is there another way? I have changed the names below to protect the innocent.
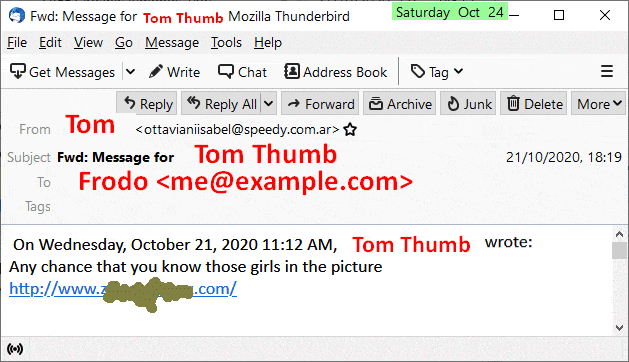
I am sure it isn't random chance as I don't get similar emails from people I don't know.
How does the spammer work out that
- Frodo and Tom know each other,
- Tom's surname is Thumb, and
- get both their email IDs?
Is this possible? Probable? Or is there another way? I have changed the names below to protect the innocent.